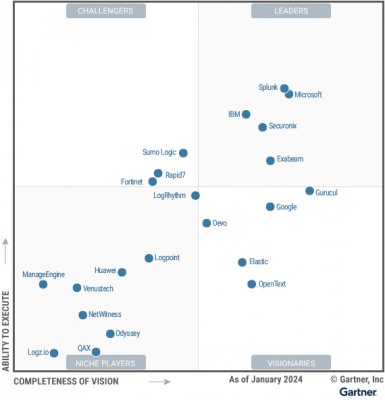
The march toward the cloud for data and services has many companies rethinking their approach to cyber security. Do they need a cloud security strategy? What is different about a cloud security strategy? Recent surveys have shed light on how security strategies are changing and, more important, how they should change.
Placing more IT infrastructure in the cloud is in some ways more secure than having it in-house. For instance, you can be reasonably sure that the system is running the latest version, with the proper patches in place. Cloud service providers are also building in new capabilities, such as using machine language for anomaly detection. However, it also presents new risks, some of which is the result of misunderstanding how to manage cloud security.