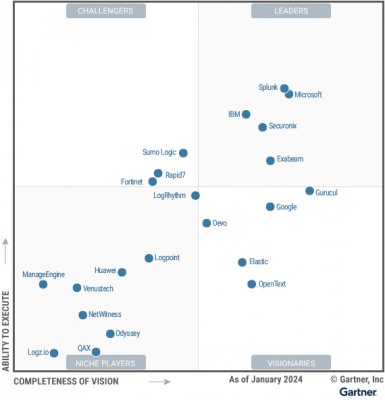
Highlights:
- Web application programming interface security often overlooks attack detection, evident in vendors’ scarcity of dedicated API attack detection tools. However, companies must recognize that API security goes beyond discovery and authentication.
- Assume all input arriving at a server application programming interface is potentially malicious. Employ API gateways and Web Application Firewalls (WAFs) for schema validation and attack protection at layer 4 and layer 7 as your first line of defense.
Application Programming Interface (API) security and data management is crucial for organizational success. As C-suite executives, you understand the importance of staying ahead of cyber threats to uphold your brand’s integrity and maintain customer trust.
Consider this: implementing robust application program interface security measures for high-ROI defends your organization against potential breaches and showcases your commitment to reliability and customer-centric values. Each security measure fortifies your company’s defenses and elevates its reputation as a trusted industry pioneer.
APIs provide a foundation for innovation and digital transformation, but organizations struggle to secure their APIs, and API-related breaches are common.
To fully address API security, pay attention to governance, discovery, testing, authentication and authorization, protection, detection, response, and your use of third-party APIs.
Let us look at what key components security leaders need to equip themselves with in an API security program.
Components Of Application Programming Interface Security to Enhance ROI
Securing APIs is crucial for protecting sensitive data and maximizing return on investment.
Critical components of API security to fuel ROI include the following:
-
Adopt automation and federated approach to effective API governance
API governance is crucial, yet it often hampers API delivery with significant bottlenecks and slowdowns. Forrester’s observations reveal that API governance can delay time to market to such an extent that organizations shy away from mentioning “governance” due to its negative connotations.
This issue arises primarily from using one-size-fits-all and bureaucratic, centralized governance approaches. While centralized governance may initially seem appropriate, successful organizations swiftly transition to federated governance models guided by central policies, acceptable risk thresholds, and performance metrics.
They customize governance for each API based on its unique risk profile rather than applying a uniform approach. Forrester notes a growing trend towards leveraging automation to enforce and audit API governance standards, ensuring greater consistency in a federated governance framework.
-
Incorporate attack detection to help your API security plan grow
Web application programming interface security often overlooks attack detection, evident in vendors’ scarcity of dedicated API attack detection tools. However, companies must recognize that API security goes beyond discovery and authentication.
Attackers exploiting API credentials, misconfigurations, or protocol downgrades can evade standard policy-based protections. Real-time automated attack detection becomes crucial here, identifying anomalous traffic and patterns.
Choose a vendor that comprehends your business context, API architecture, and usage to establish appropriate rules and policies. Effective real-time detection should cover all APIs to safeguard against known threats and suspicious activities.
-
Close authenticity and authorization gaps
Authentication and authorization are recurring themes in the recent OWASP Top 10 API Security Risks for 2023, highlighting issues like broken object-level authorization, broken authentication, and broken function-level authorization.
Several high-profile API-related breaches, such as the Optus breach last year, have been attributed to authentication or authorization failures.
API security has been scrutinized following such incidents, with CIOs, CISOs, and SOC managers prioritizing application programming interface security assessments for ROI-driven assessments. Proper authentication starts with discovery, as unidentified API endpoints pose significant risks.
While API gateways manage API availability to clients, configuring API security remains essential. Experts recommend prioritizing OAuth over API keys for authentication and authorization, emphasizing the importance of ensuring that authentication flows operate as intended.
-
Put in place API security policies to prevent known problems in advance
Effective protection policies are crucial for securing your assets. Start by ensuring your policies include API-specific rules to defend against OWASP API Security Top 10 vulnerabilities. Tailor these policies for regional, industry-specific, and company-specific contexts, API usage, and trust models.
Protection and trust models should operate at various points: in front of the API, at the API interface entry point, or within the API implementation itself. Policies may be applied declaratively or require custom coding.
Assume all input arriving at a server application programming interface is potentially malicious. Employ API gateways and Web Application Firewalls (WAFs) for schema validation and attack protection at layer 4 and layer 7 as your first line of defense. This multi-layered approach helps mitigate risks and ensures a comprehensive security posture.
A breach occurs even with solid security measures in place. Analyzing actual API security breaches offers essential insights into typical flaws and the possible repercussions of insufficient security precautions. Here are a few noteworthy instances:
What Are Some Examples of Application Programming Interface Security?
API security breaches can have severe consequences, exposing sensitive data and critical functionalities to unauthorized users.
Here are some notable examples of such breaches:
- T-Mobile API Breach (2022): T-Mobile reported that a threat actor accessed the personal information of 37 million postpaid and prepaid customer accounts through one of its APIs.
- Equifax API Breach (2017): Equifax suffered a massive data breach, exposing sensitive data of over 143 million customers. Hackers exploited a vulnerability in Equifax’s API, accessing the data without proper authentication.
- Strava API Breach (2018): Strava, a fitness app, inadvertently revealed sensitive information about military bases worldwide. This breach occurred because a vulnerable API transmits users’ location data online.
These real-world cases underscore the importance of implementing robust security measures to protect APIs. It is crucial to employ rigorous security testing methods to safeguard APIs effectively. By understanding the common vulnerabilities through these examples, businesses can better appreciate the need for comprehensive API security testing methods.
What Are the Methods of Application Programming Interface Security Testing?
You can use the following methods to test your APIs for security vulnerabilities manually:
-
Test for Parameter Tampering
Parameter tampering involves manipulating parameters sent through API requests to alter the intended behavior. For instance, an attacker might change the purchase amount or access unauthorized data.
- Identify hidden fields: Use the browser’s element inspector to find hidden form fields.
- Experiment with values: Modify the values of these hidden fields and observe how the API responds. This can reveal if the API correctly validates and authorizes requests.
-
Test for Command Injection
Command injection attacks involve injecting operating system commands into API inputs to execute unauthorized actions on the server.
- Inject commands: Insert OS-specific commands into API inputs. Enter a benign command followed by a command that should not normally be run, such as and and cat /etc/passwd to test for command injection.
- Example input: ping 8.8.8.8 and and cat /etc/passwd
-
Test for API Input Fuzzing
Fuzzing involves sending random or unexpected data to the API to uncover vulnerabilities.
- Send random data: Input large numbers, negative values, zero, or random strings, including SQL queries and system commands.
- Observe responses: Look for errors, incorrect processing, or crashes that indicate potential security issues.
- Test for unhandled HTTP methods: To interact with web applications, APIs use various HTTP methods (POST, GET, PUT, PATCH, DELETE). Unsupported methods can create vulnerabilities if not properly handled.
- Check supported methods: Send HEAD requests to API endpoints requiring authentication and try standard HTTP methods to see if they are appropriately managed.
- Example methods: Test with POST, GET, PUT, PATCH, DELETE, and observe the server’s response.
- Implementing These Tests
- Use browser tools: Inspect the element and modify hidden fields.
- Command line tools: Use ‘curl’ or similar tools to inject commands and test HTTP methods.
- Fuzzing tools: Employ automated fuzzing tools or write scripts to send random data inputs.
By manually testing API security with these methods, you can identify and address potential security vulnerabilities, improving the overall security posture of your applications.
Future of API Security
Application Programming Interface (API) Security is paramount as digital transformation accelerates. Implementing a robust defense strategy with API best practices in access controls, input validation, and encryption is crucial.
Proactive testing identifies vulnerabilities, but evolving attack tactics necessitate advanced technologies like AI, machine learning, and blockchain for improved threat detection and response.
Despite technological measures, human factors remain essential. Cultivating a security-focused culture and ongoing training sustains high standards. Given the strategic risks posed by cyberattacks, safeguarding APIs ensures operational resilience and trust, making security a business enabler.
Enhance your expertise with our exclusive collection of security-related whitepapers and in-depth reports.