Highlights:
- Achieving full control over modern web application security requires adopting customized processes to tackle the challenges of complex, large-scale, cloud-native applications.
- Newer security tools identify and defend against vulnerabilities based on their threat level to the environment.
While web applications and their security have been enduring challenges, their nature has gone through a major shift. Traditional monolithic setups on individual servers have given space to containerized, distributed, cloud-native applications.
However, this move presents novel security concerns, especially with the evolving dependence on APIs for internal communication and external connectivity. With the average application now relying on numerous APIs, the attack surface enlarges, posing concerns in authorization, authentication, and data privacy.
Moreover, the well-known adoption of public clouds also complicates security, as traditional perimeter defenses are no longer efficient in an era of constant exposure to internet-based threats.
While some microservices can still be protected by firewalls, scenarios demanding external data interaction or third-party API access disobey internal network boundaries, requiring a recheck of security techniques. So, there is a need for comprehensive modern web application security practices for integrated solutions.
Modernizing Web Application and API Security
Gaining full control over modern web application security demands adopting customized processes that tackle the challenges of distributed, complex, and large-scale cloud-native applications.
This blog highlights five best practices to secure modern web applications and APIs, providing an agile, holistic, and modern approach in comparison to conventional processes like WAF or API gateway.
The practices below improve overall security and provide flexibility to adapt to distinct architectures. Since security demands differ between organizations, the guidelines provided help update security approaches for web applications and APIs across any cloud-native architecture, guaranteeing linking with rising complexities and threat landscapes in a cloud-first, API-centric environment.
How to Attain Modern Web Applications Security: Best Practices for Security Teams
Securing modern web application architecture demands more than conventional strategies and tools. Additional practices are also needed to tackle the security issues of complex, large-scale cloud-native applications.
These practices of securing modern web applications provide a holistic, agile approach beyond traditional WAFs or API gateways. Also, it improves overall security and offers flexibility for unique web architectures.
Since security needs differ, these guidelines assist enterprises in modernizing their security for any cloud-native architecture, keeping pace with new concerns and threats in a cloud-first, API-centric world.
Practice 1: Explore Cloud-agnostic Security Solutions
The majority (92%) of businesses currently utilize various public clouds, with 80% adopting hybrid cloud architectures that merge private and public cloud resources, according to CMSWire.
For web applications and API security, this means that depending only on security tools crafted for a single cloud environment is not enough now. Today’s teams expect a cloud-agnostic perspective on security to recognize and tackle security concerns across any cloud environment and architecture.
Despite issues such as varying workload names and virtual network configurations across different public clouds, guaranteeing security across all cloud types is crucial for protecting web applications and APIs, irrespective of hosting location. For this, security solutions must be employed at the workload level within each host, VM, container, or serverless function.
The best way to secure modern web applications and APIs and fix issues like access control misconfigurations or insecure API authentication is by placing security controls directly on the workloads.
Implementing security controls at the workload level secures constant security across various infrastructures, containing multicloud and hybrid cloud setups, reducing issues related to the location of web applications.
Practice 2: Implement Priority-based Risk Management
Thousands of security vulnerabilities are recorded in databases like NIST NVD, with nearly 22,000 new ones discovered in 2021 alone, as per Comparitech.
However, not all vulnerabilities are similarly complex, and many can only be under specific conditions. Whether your web applications and APIs are at risk relies on elements like environment configurations, software library versions, and the type of attack. Recognizing which vulnerabilities create the biggest threat is essential for an effective response.
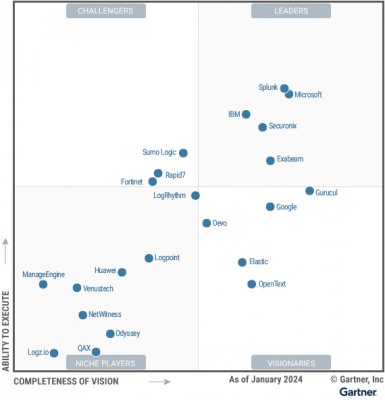
By categorizing high-risk vulnerabilities, teams can effectively streamline risks while improving security posture. Newer security tools identify vulnerabilities as well as defend against them based on how much they threaten the environment. Understanding which vulnerabilities require urgent action authorizes smart responses to security risks.
Practice 3: Move Web Application Security to the Left
While guiding and scanning web applications and API traffic in production environment is essential, it’s also crucial to highlight risks before deploying applications into production whenever possible.
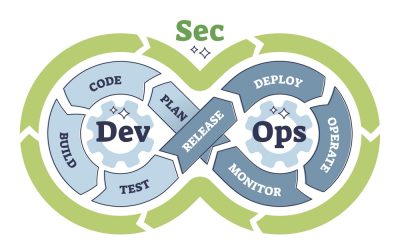
This practice, known as shifting security “left,” makes teams to uncover risks earlier in the software development lifecycle, guaranteeing that security concerns are tackled before impacting production environments.
Shifting security left promotes quicker and more cost-effective resolution of security issues, as it’s easier to address risks before software goes live. Cooperation between application security, development, and DevOps teams is paramount for successfully shifting security left.
To gain this collaboration, customers expect a solution that is efficient in analyzing code repositories and image libraries and integrating them with popular CI/CD tools. By shifting security left, teams can highlight vulnerabilities early in the software delivery pipeline, making them to tackle concerns before deployment to production.
Practice 4: Adopt All-inclusive Security Solutions
Streamlining security tools for web applications is a need. Instead of juggling various solutions for various threats like OWASP Top 10 risks, DoS attacks, or API and bot attacks, select an integrated, unified security toolset. It is one of the best practices of modern web application security for integrated solutions.
This approach eases management, lowers oversight, and authorizes comprehensive protection. By deploying a single solution, including everything from application firewalls to vulnerability detection and API security, you retain time and gain confidence in your defenses.
With the uncertain nature of cyber threats, a comprehensive approach makes you ready for anything, whether an access control exploit, botnet attack, or security misconfiguration.
By including all bases, you’re ready to combat threats across the spectrum, starting from application layer attacks to API vulnerabilities.
Practice 5: Use Various Layers of Defense
While it’s enticing to believe in attaining 100% protection against web-based attacks, the reality is not the same, with over 2,200 daily attacks on average, as per Norton. To tackle this, deploying multiple layers of defense is key.
These layers authorize that if attackers avoid one defense, they won’t jeopardize the whole environment. This strategy is often likened to the “Swiss cheese model,” which reduces cybersecurity risks by layering defenses.
Starting with visibility and management of attack surfaces, followed by regulations for both inbound and outbound traffic, like vulnerability scanning and strong authentication, and securing infrastructure layers like hosts and containers guarantees all-inclusive protection.
By following these layers, the chances of successful attacks are reduced significantly.
Concluding Remarks
Security teams might find it easy if we still had simple monolithic web applications, but that phase is over. Today’s cloud-native, API-centric modern web applications and microservices give us new security challenges.
This complexity demands new security practices that complement traditional methods, certifying flexible, scalable, and multilayered security for any environment and workload.
The above practices of securing modern web applications offer a comprehensive, agile solution that goes beyond traditional WAFs or API gateways. Additionally, they enhance overall security and provide flexibility for diverse web architectures.
Enhance your understanding by delving into various security-related whitepapers accessible through our resource center.