Highlights:
- If a security issue arises in one environment, fixes can be applied to the IaC scripts and uniformly deployed across all other environments, ensuring consistency and bolstering security measures.
- By embedding IaC scanning and security-as-code fixes throughout the DevOps lifecycle, you can embrace a more modern approach to cloud security. As with adopting any new technology, IaC can introduce new complexity and risk—primarily when several frameworks are used across teams.
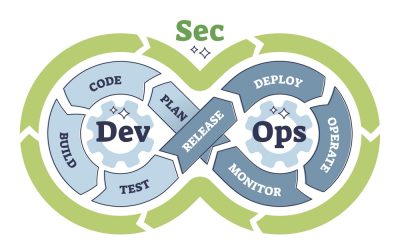
In the infrastructure as Code (IaC) security, DevOps entails a close collaboration between developers and DevOps engineers, integrating IaC into continuous deployment practices. Enter “DevSecOps,” the “shift-left approach,” which involves embedding security considerations into DevOps processes.
For infrastructure as code security for business cost-cutting, DevSecOps emphasizes integrating security from project inception and maintaining stringent security measures throughout. This approach also involves leveraging suitable tools tailored to the workload and automating security processes (sometimes called security as code).
Beyond technology, DevSecOps embodies an organizational culture characterized by seamless information flow across diverse teams. It advocates for automation across all levels, emphasizing the importance of IaC, which automates entire deployment processes.
In the DevSecOps framework, IaC’s role extends to automating security best practices and employing tools suited to specific workloads to enhance security measures.
How Does Infrastructure As Code Improve Security and Budget Discipline?
Infrastructure such as Code (IaC), which has historically been employed for automating business infrastructure procedures, possesses significant potential as a robust tool for enhancing cloud security.
Here are several ways in which IaC can prove vital to bolstering the security of cloud environments:
-
Simplifying audits and compliance
Optimizing compliance and audit procedures is an essential function of infrastructure as code in cloud security for resource allocation. Today’s businesses must adhere to various industry data security and privacy regulations.
With IaC, the entire infrastructure configuration is scripted and version-controlled, facilitating easy monitoring of changes and maintaining an audit trail to streamline compliance efforts.
IaC offers a transparent and easily understandable depiction of the infrastructure layout. This clarity greatly benefits auditors reviewing systems to verify compliance with security standards.
By providing a clear view of the infrastructure, security infrastructure as code ensures comprehensive scrutiny of all aspects, saves time, and mitigates the risk of oversight.
-
Maintaining uniformity
IaC ensures consistency across all environments, a critical element in maintaining secure IT systems.
Historically, IT infrastructures were vulnerable to configuration drift, where running servers deviated from their original configuration due to manual updates and patches, leading to security vulnerabilities.
With IaC, this risk is mitigated as it provides sustainable IT infrastructure. By defining infrastructure in code, every environment becomes identical, minimizing inconsistencies.
If a security issue arises in one environment, fixes can be applied to the IaC scripts and uniformly deployed across all other environments, ensuring consistency and bolstering security measures.
-
Security policy automation
Automating security policies is a crucial facet of infrastructure as code security for fiscal efficiency. In traditional IT setups, enforcing security policies manually was prone to human error or oversight.
However, IaC can encode security policies into the infrastructure, ensuring consistent enforcement across all environments. This automation minimizes the risk of human error and guarantees that all deployments align with the company’s security standards.
-
Enabling immutable infrastructure
IaC also enables the adoption of an immutable infrastructure architecture model, where servers are never altered post-deployment.
Instead, changes necessitate the creation of new servers from a standardized template while decommissioning older ones. This methodology heightens security by minimizing the attack surface for potential threats.
The consistent nature of the infrastructure allows for prompt detection and resolution of unauthorized changes or anomalies.
Furthermore, it prevents unauthorized access or modifications, as each deployment is fresh and devoid of potentially compromised configurations from prior iterations.
-
Increasing incident response time
In a security incident, security testing infrastructure as code aids operational efficiency, enabling swift response capabilities. Infected servers can be decommissioned and replaced with clean instances using IaC scripts.
This rapid response minimizes downtime and potential damage, facilitating swift recovery and uninterrupted business operations.
By facilitating the rapid remediation of security threats, IaC fortifies the resilience of cloud infrastructures against cyberattacks.
This assurance empowers businesses to operate securely in the digital realm, knowing they can swiftly address and mitigate security incidents as they arise.
Let’s shift focus from the conceptual advantages of IaC software and explore tangible success stories showcasing its revolutionary potential in action.
Real-world Infrastructure as Code Success Stories
Numerous top-tier companies have experienced infrastructure advantages, such as IaC. These anecdotes showcase how organizations have leveraged IaC to bolster security measures, maintain budget discipline, and achieve operational excellence:
- Barclays: This global bank embraced IaC, facilitating quicker IT deployments and enabling a more agile response to market fluctuations.
- General electric: GE’s IT department leveraged infrastructure as code security scanning for financial streamlining. It could oversee its expansive cloud infrastructure, enhancing operational efficiency and decreasing expenses.
- Walmart: Utilizing IaC, Walmart has streamlined its Ecommerce operations, allowing for seamless scalability, particularly during peak periods such as Black Friday.
Let’s delve into actionable tips for seamlessly integrating Cloud DevSecOps principles with IaC to enhance your cloud-based infrastructure management and security protocols.
Tips for Embracing Cloud DevSecOps and IaC
As organizations increasingly pivot towards cloud infrastructure to fuel innovation and agility, integrating DevSecOps practices becomes imperative to uphold robust security standards and ensure seamless operations.
These are the three things you can do to overcome those challenges:
#1 Automate everything
Your engineering teams are likely already automating much of your software testing, encompassing tasks like unit testing and dependency scanning. Similarly, cloud security should be automated to ensure robust protection.
Automated scanning is crucial for systematically applying security and compliance measures across complex cloud environments, eliminating the need for manual documentation review.
To achieve this, it’s essential to leverage proper tooling through commercial solutions or open-source tools like Checkov to automate the detection and resolution of security issues.
#2 Leverage existing processes
Surfacing actionable feedback at the wrong time or context can lead to noise and reduced productivity. The key to successfully adopting DevSecOps in the cloud is integrating it seamlessly into the tools and processes developers rely on now a days.
Fortunately, the foundation for embracing automation and security as code is often already established. Determining where and how to enforce guardrails depends on your existing toolset, organizational objectives, and security maturity level.
#3 Secure in code
The friction in DevSecOps often arises from a reactive security mindset, which focuses on issue monitoring rather than prevention.
Infrastructure as code security software can transform this mindset into a proactive approach, enabling governance automation in a common language for security practitioners and DevOps engineers.
Enforcing policies at the code layer ensures consistent cloud security application and scalability over time, leading to long-term resource savings.
However, addressing infrastructure security throughout each phase of the DevOps lifecycle is crucial, especially considering the limited information available in the early stages.
Conclusion
Infrastructure as Code (IaC) enhances the efficiency of deploying and managing infrastructure and is vital for enabling cloud DevSecOps. Despite its own challenges, IaC can be utilized to secure your infrastructure.
By integrating IaC scanning and security-as-code solutions throughout the DevOps lifecycle, you can adopt a more modern approach to cloud security.
As with adopting any new technology, IaC can introduce new complexity and risk—primarily when several frameworks are used across teams.
Because it can also run in parallel with manual cloud orchestration, implementing IaC without full adoption and visibility can lead to gaps in how resources are provisioned and, most importantly—secured.
The benefits of IaC generally outweigh the costs, allowing for automation, scalability, and repeatability in cloud provisioning and management.
Elevate your knowledge with our exclusive collection of security-related whitepapers and reports.